Cybersecurity is unique. Unlike other technical fields that can be learned in isolation, cybersecurity sits at the intersection of multiple IT domains, requiring both broad understanding and deep expertise to be truly effective.
The Problem with Traditional Learning Approaches
Most people try to learn cybersecurity by either:
- Going too deep too early without the suffcient foundation: Diving into advanced security topics without understanding underlying IT systems leads to superficial knowledge that breaks down under pressure.
- Staying too broad: Learning a little about everything but never developing true expertise.
- Following random paths: Jumping between topics without a structured progression and never developing deep understanding.
Why Cybersecurity is Different
Cybersecurity has unique characteristics that make the inverted T approach particularly effective:
a) Cybersecurity is a Specialization, Not a Domain in Itself
You can't secure what you don't understand. Effective cybersecurity requires knowing how networks route traffic, how applications handle data, and how systems interact, it's not just about security tools and techniques.
b) Interconnected Domains
Security threats don't respect domain boundaries. A single attack might involve network exploitation, application vulnerabilities, identity compromise, and data exfiltration. Understanding these connections is crucial.
c) Rapidly Evolving Landscape
New threats, technologies, and attack vectors emerge constantly. Having broad foundational knowledge helps you adapt and understand how new developments impact different areas. Remember, you don’t have to be an expert in each area, but knowing enough can help you make better decisions.
Three Layer Progression
A wholistic cybersecurity plan looks something like this:
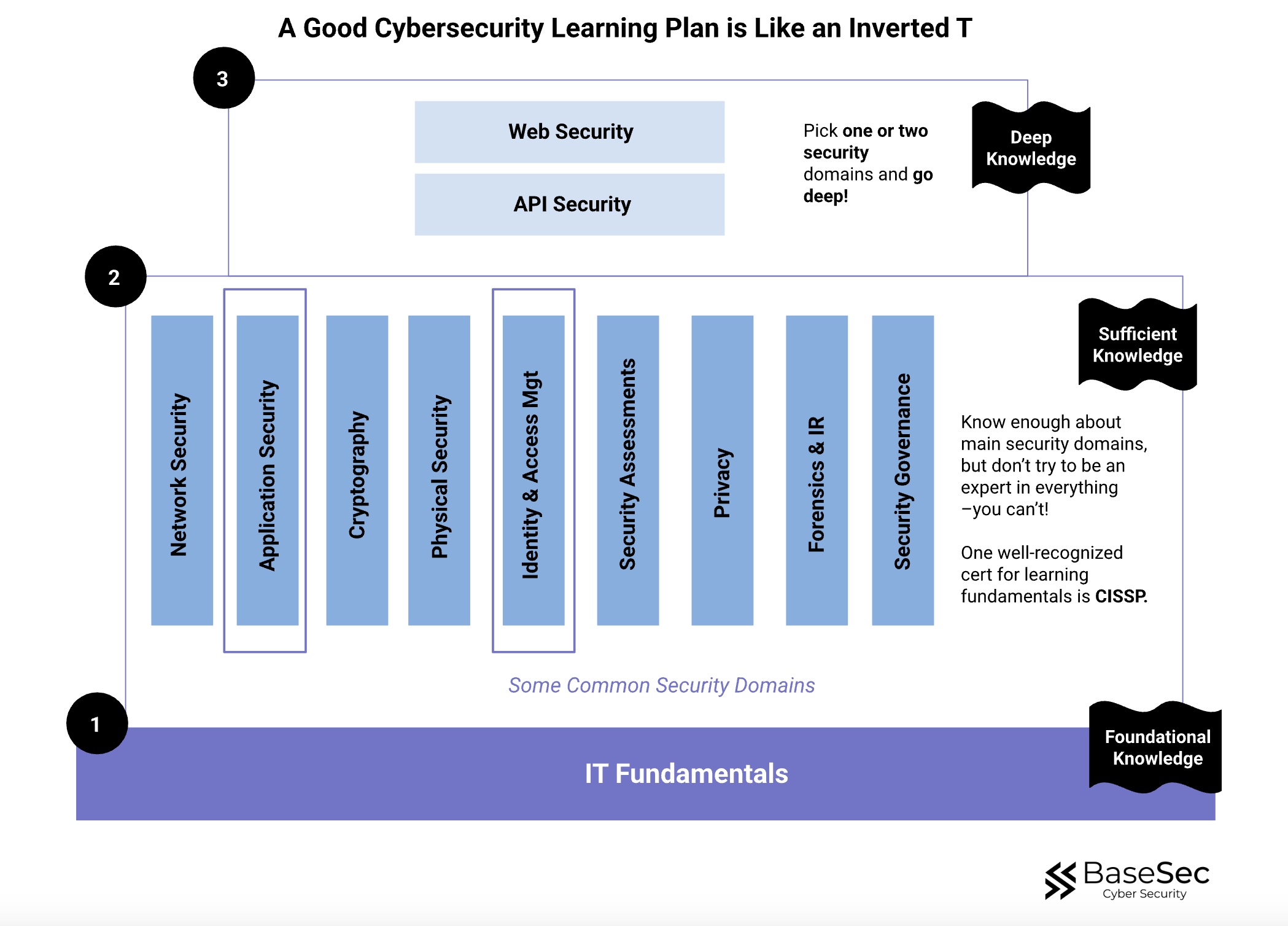
Layer 1: IT Fundamentals (Foundational Knowledge)
Build the technical foundation that underlies all security concepts. Without understanding how networks, systems, and applications work, security controls won't make sense.
Key Goal: Know how IT systems (and teams) work.
Layer 2: Security Domain Awareness (Sufficient Knowledge)
Develop enough understanding across all major security domains to:
- Recognize how threats span multiple areas
- Communicate effectively with specialists in other domains
- Make informed decisions about security threats
- Evaluate vendor claims and industry discussions critically
Key Goal: Know enough to identify misinformation and ask intelligent questions, but don't try to become an expert in everything.
Layer 3: Deep Specialization (Deep Knowledge)
Choose 1-2 domains where you'll develop true expertise. This focused approach allows you to:
- Become genuinely valuable as a security professional
- Advance your career with clear expertise
- Be able to solve complex problems that automation can’t easily solve
Key Goal: Depth and expertise in your chosen area.
The Bottom Line
The inverted T approach recognizes that cybersecurity is fundamentally interdisciplinary. By building broad awareness before deep specialization, you develop both the foundational knowledge to be effective and the specialized expertise to be valuable. This combination creates security professionals who can think holistically while contributing meaningfully to specific technical challenges.


